Published
- 42 min read
Introduction to Blockchain Immutability and Redaction

How to Write, Ship, and Maintain Code Without Shipping Vulnerabilities
A hands-on security guide for developers and IT professionals who ship real software. Build, deploy, and maintain secure systems without slowing down or drowning in theory.
Buy the book now
Practical Digital Survival for Whistleblowers, Journalists, and Activists
A practical guide to digital anonymity for people who can’t afford to be identified. Designed for whistleblowers, journalists, and activists operating under real-world risk.
Buy the book now
The Digital Fortress: How to Stay Safe Online
A simple, no-jargon guide to protecting your digital life from everyday threats. Learn how to secure your accounts, devices, and privacy with practical steps anyone can follow.
Buy the book nowIntroduction
Blockchain technology is fundamentally a decentralized, append-only digital ledger where data (typically transactions) are grouped into blocks that are cryptographically linked in sequence. Each block contains a cryptographic hash of the previous block, forming a chain that guarantees data integrity and a tamper-proof record [1]. In essence, once a block is added and confirmed by the network’s consensus process, it becomes extremely difficult to alter any information in that block without invalidating all subsequent blocks. This property of immutability – where records “once recorded, cannot be modified or erased” [2] – is celebrated as a key security feature of blockchains. It builds trust in systems like Bitcoin and Ethereum by ensuring that transaction history is permanent and verifiable.
However, the absolute immutability of traditional blockchains can also be a double-edged sword. On one hand, it prevents fraud and unauthorized changes; on the other hand, it means that incorrect or illicit data recorded on-chain is virtually impossible to remove. This has led to notable concerns: for example, researchers and law enforcement (Interpol) have flagged that harmful or illegal content (like child pornography or malware) has been embedded in public blockchains (e.g. via data fields in Bitcoin transactions), which then cannot be purged [3] [4]. Additionally, data privacy regulations such as the EU’s “Right to be Forgotten” (GDPR) conflict with blockchain’s permanent record – once personal data is on-chain, how do you delete it upon request? These challenges have spurred interest in making blockchains redactable under certain circumstances, i.e. editable blockchains that preserve most benefits of immutability while allowing authorized edits or removals for compliance, error correction, or legal reasons [5].
In this article, we provide a comprehensive overview of redactable blockchains – blockchains designed to allow modifications to the ledger’s history in a controlled manner. We start with how traditional blockchains function and achieve integrity, then delve into the mechanisms that enable redaction (particularly chameleon hashing for collision-tolerant hash linking). We compare redactable vs. regular blockchains in terms of integrity guarantees, transparency/auditability, and regulatory compliance. Next, we survey the current state of research and developments in this area – including covert channels, and recent implementations (e.g. an opensource prototype by Ken Lina on GitHub). We then explore an intriguing implication: how the ability to edit blockchain history could be exploited to create covert channels. We explain what covert channels are in a security context and outline how they might be implemented via blockchain edits. Concrete attack vectors and proof-of-concept ideas are discussed based on existing implementations. We conclude by summarizing the implications for cybersecurity and highlighting open research questions raised by this new paradigm of “mutable” blockchains.
How Traditional Blockchains Ensure Immutability
To appreciate redactable ledgers, it’s important to understand how and why blockchains are traditionally immutable. In a standard blockchain (like Bitcoin’s or Ethereum’s), each block contains a hash pointer to the previous block. This hash pointer is essentially the cryptographic digest (e.g. SHA-256) of the entire previous block’s contents. As a result, any change to an earlier block (even flipping one bit of transaction data) would completely change its hash, thereby breaking the chain because the subsequent block would no longer contain the correct pointer. The offending block and all blocks after it would be invalid in the eyes of nodes verifying the chain. In practice, an attacker would have to recompute that block and every following block’s hash (and also outpace the network’s consensus, e.g. Proof-of-Work difficulty) to make the change “stick,” which is computationally infeasible once the chain has grown sufficiently. This design makes the ledger append-only and tamper-evident – once data is recorded and confirmed by consensus, it cannot be altered without detection.
Regular blockchains thus prioritize data integrity and transparency above all: every participant sees the same history, and any attempt to rewrite history is obvious (and rejected by honest nodes). This is ideal for trustless environments, ensuring that fraudulent modifications are virtually impossible. But as noted earlier, this inflexibility can be problematic when genuine mistakes or unlawful content enter the ledger. For example, if someone accidentally publishes a piece of sensitive personal information or illegal material into a block, that artifact becomes permanent on the distributed ledger. Even if it is not easily accessible, its mere presence can be a compliance nightmare.
The tension between immutability and legal/ethical requirements for data deletion has prompted researchers to seek a compromise: can we allow edits on a blockchain without sacrificing the chain’s integrity? This is where redactable blockchain concepts come in.
What Are Redactable Blockchains?
A redactable blockchain (sometimes called an editable or mutable blockchain) is a blockchain that provides a mechanism to modify or remove data from blocks post-publication in a controlled manner without breaking the chain’s cryptographic integrity. In a redactable blockchain, authorized participants (or a governance process) can rewrite history under certain conditions – for instance, to erase illicit content, correct errors, or comply with regulatory orders – and the chain will remain valid as if the data had been that way from the start. Crucially, these modifications should not allow unauthorized tampering; they are typically governed by strict policies or consensus (e.g. a majority vote, a special administrator key, or a multiparty agreement) so that only approved changes occur.
How can the chain remain intact if a block deep in the history is changed? The core idea is to replace the standard cryptographic hash linking with a more flexible alternative that supports predetermined collisions. The most prominent tool enabling this is the chameleon hash function.
Chameleon Hashing: The Key to Controlled Rewrites
A chameleon hash is a collision-resistant hash function with a trapdoor. Under normal circumstances (without the trapdoor key), a chameleon hash behaves like any secure hash – it’s infeasible to find two different inputs that produce the same output hash value. However, with knowledge of a secret “trapdoor” key, one can efficiently find collisions for the hash [6][7]. In other words, an authorized party holding the trapdoor can take an existing hashed message and generate a different message that hashes to the exact same value. This property is the linchpin of most redactable blockchain designs.
In a redactable blockchain implementation, the hash that links block Bi to Bi-1 is replaced with a chameleon hash. Initially, when block Bi is created, it includes (in its header) the chameleon hash of the previous block’s hash and its own data. Typically, this involves some randomness: each block might contain an extra random nonce (sometimes called r or a “chameleon hash check value”) [8]. This random value is chosen such that H(datai, ri) = digesti, where digesti will be stored in block Bi+1 as the link. Without the trapdoor, no one can easily find an alternative (data’i, r’i) that yields the same digest. But if an authorized editor decides to modify block Bi (say, to redact some content), they can use the trapdoor key to compute new values (data’i, r’i) that produce the exact same hash as the original [9] [8]. The block is then replaced with the new data and new hash nonce, and because the resulting hash (digest) is unchanged, block Bi+1 and the rest of the chain remain oblivious to the change - the chain links don’t break. Essentially, the editor has “surgically” altered the blockchain’s history while preserving the hash pointers.
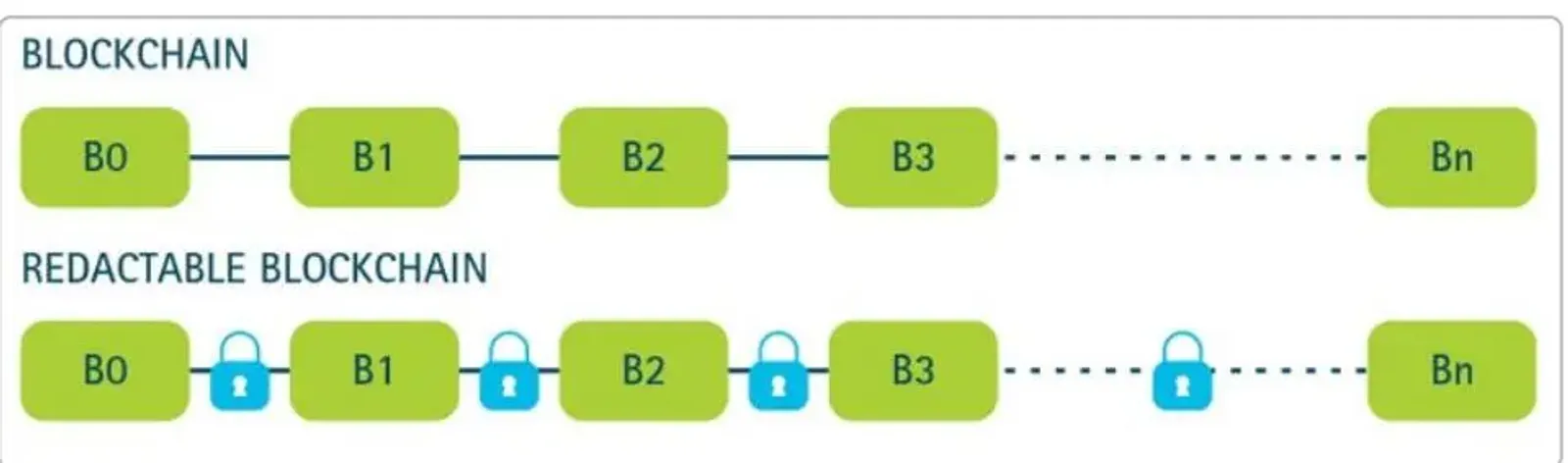
Illustration: In a traditional blockchain (top), blocks B0–B3 are locked in by one-way hash links – altering block B1 would change its hash (solid line), breaking the chain at B2. In a redactable blockchain (bottom), special trapdoor-enabled hash links (denoted by padlock icons ) allow an authorized party to “unlock” a link, modify a block (e.g., B1 or B2), and recompute the hash so that the chain remains intact. Source and copyright: Accenture
This approach was first formalized by Giuseppe Ateniese et al. (2017), who proposed integrating chameleon hashes into blockchain to allow block-level rewrites [10]. Around the same time, Accenture built a prototype editable blockchain for enterprise use, co-developed with Ateniese, using chameleon hashing under the hood [11][12]. In Accenture’s design (targeted at permissioned blockchains), designated administrators with the trapdoor key could “unlock” a block’s hash pointer and edit or remove that block’s data without breaking the chain [12]. Importantly, they suggested governance rules and even an “immutable scar” – an indelible marker that a block was edited – to keep an audit trail [13]. The core cryptographic trick, however, was exactly as described: use a modified chameleon hash as the linking mechanism, so that history is no longer absolutely permanent – it can be rewritten if you hold the right key.
From a technical standpoint, a chameleon hash function has two sets of keys: a public hash key (used to compute the hash value for given data) and a private trapdoor key (held by the entity or committee allowed to redact). Formally, it provides: (i) a hashing algorithm that anyone can use to get H(data) $\rightarrow$ digest (like normal hashing), and (ii) a collision finding algorithm that only the trapdoor holder can execute to find an alternate data’ such that H(data) = H(data’) [14] . It is collision-resistant for those without the trapdoor (ensuring outsiders cannot maliciously forge collisions) [7]. Thus, the blockchain remains tamper-proof to the public (they can’t change it) but malleable to authorized parties. The integrity of the chain is preserved in that every block still links consistently – but we’ve introduced a carefully regulated loophole to modify contents.
Variations and Security of Redaction Mechanisms
Early implementations of redactable blockchains using a single trapdoor key raised natural concerns: if one entity can change anything, doesn’t that reintroduce a trusted third party? What if the key is misused or leaked? Subsequent research has refined the concept to address these issues:
Threshold Schemes & Distributed Keys: Rather than a single administrator, the power to redact can be distributed among a group. For example, a threshold chameleon hash requires M-of-N parties (a “redaction committee” or jury) to cooperate to produce a collision [15]. This prevents unilateral edits and makes unauthorized redaction harder (an attacker would need to corrupt many parties). The RedactChain prototype (2023) follows this approach: it outsources redaction decisions to small juries of nodes that jointly hold the trapdoor capability via threshold cryptography [16]. Only if a quorum agrees a transaction should be removed will they compute the collision and publish the redacted block. This adds decentralization and accountability – no single party holds all the power [17].
- Consensus-Vote Based Redaction: In permissionless settings, one cannot assume a fixed admin or committee. Some proposals make redaction an operation that must be voted in by miners or token holders. For instance, a 2019 protocol by Deuber et al. uses a consensus-based voting: if a proposed redaction garners enough votes on-chain, the change is executed [18]. The redaction might be implemented by having miners incorporate the new block content once approved. This avoids any single trapdoor key altogether but can be slower (needing many blocks to vote) and is limited by voter participation.
- Audit Logs & Transparency: To balance transparency, systems often include a way to mark or log that a redaction occurred. One idea (as Accenture suggested) is that even though the old data is overwritten, a scar remains – e.g., a flag in the block header or a public log entry – so that observers know a particular block was modified [13] . Some schemes allow the original hash to be “broken” in a detectable way unless a special audit key is used to verify it, ensuring that any altered block can be identified by those auditing with the appropriate keys [11][12]. Other designs support traceability where the system retains an encrypted copy of the original data or a diff, so authorized auditors can see what was changed. These measures aim to prevent silent, undetectable history rewrites.
Despite these safeguards, a redactable blockchain inherently trades some of the pure immutability of traditional chains for flexibility. The integrity model shifts from “any change is impossible” to “changes are possible, but only by authorized actors under defined rules.” In practice, this could be acceptable or even desirable in enterprise and government use-cases (where regulation compliance is critical), but it introduces new security questions which we’ll explore later. First, let’s explicitly compare how a redactable blockchain stacks up against a conventional one on key properties.
Redactable vs. Regular Blockchains: Integrity, Transparency, Compliance
Implementing an “edit-friendly” blockchain affects several foundational properties of the system. Here’s a comparison along three important dimensions:
Data Integrity & Security: A conventional blockchain offers strong integrity: once data is in the • ledger and confirmed, users can be confident it hasn’t been altered. The only way to change it would be to attack the consensus (e.g., 51% attack) or use extreme computational power to remine blocks – scenarios considered infeasible for large networks. In a redactable blockchain, integrity is a bit more nuanced. The chain’s cryptographic integrity (hash links) remains intact even if data changes, which is the whole point – so on the surface, everything looks consistent. However, integrity now hinges on the security of the redaction mechanism. If the trapdoor key or majority control of the redaction committee falls into the wrong hands, an adversary could undetectably alter history. In other words, there is an insider trust assumption or additional attack surface. For example, if an attacker obtains the chameleon hash trapdoor, they could retroactively modify transactions or embed false data while still passing hash verification [21] [22]. This is mitigated by techniques like threshold keys (no single point of failure) [16] and audit logs, but it’s a trade-off: integrity is conditional on trust in certain parties or processes, rather than absolute. On the positive side, when properly managed, redactable ledgers can still be secure against unauthorized changes – e.g., proposals include formal security proofs that any redaction without consensus or without the trapdoor keys is computationally infeasible [23]. In summary, regular blockchain = immutable but inflexible; redactable blockchain = mutable with authorized integrity (integrity is preserved only so long as the special keys aren’t abused).
- Transparency & Auditability: A regular blockchain provides full transparency of history not in the sense that data is necessarily public (it can be encrypted or pseudonymous), but in that the history is an append-only log. Anyone can audit that log knowing that what’s recorded is final. In contrast, a redactable blockchain can raise questions: How do we know a given piece of data is the “original” or has it been edited? Transparency in such systems depends on design choices. Some redactable blockchains aim for “compliance-friendly transparency”, meaning that edits are allowed but visible. For instance, a separate redaction log could list all alterations that have been made, with timestamps and reasons, so that the community or regulators can review them [24]. Alternatively, as mentioned, a block might carry a marker (a scar) if it was altered [13]. In the Accenture prototype, any edit leaves an immutable scar indicating that block was altered, thereby preserving an element of accountability [13]. On the other hand, one could design the system such that edits are stealthy (no public indication), especially in a permissioned environment where the operator doesn’t want to reveal that something changed. This would obviously reduce transparency and could be problematic – users might lose confidence if they can’t tell whether data was changed behind the scenes. Most academic proposals favor accountable redactions: e.g., Derler et al. 2019 included public verifiability and accountability proofs to ensure unauthorized redactions can be detected and authorized ones are tagged in the chain [23]. Bottom line: Regular blockchains record an unalterable truth (maximally transparent), whereas redactable ones must balance editability with audit mechanisms to maintain trust. In welldesigned redactable blockchains, every change is governed and ideally publicly logged, but users must be aware that what they see could have been changed post hoc (with permission).
- Compliance and Governance: This is where redactable blockchains shine. Traditional blockchains are notoriously inflexible in meeting regulatory requirements like data privacy (GDPR) or content takedown orders. If illegal content is on Ethereum, there’s essentially no official way to remove it – law enforcement can only try to prosecute the inserter, but the data remains on every full node’s copy. Redactable blockchains, by contrast, are built to accommodate legal compliance. If a court or regulator demands certain data be expunged, a redactable blockchain used by a consortium of companies could implement that by having the authorized committee rewrite the offending block. For example, personal data removal (“right to be forgotten”) could be satisfied by overwriting a user’s data with a placeholder, and using chameleon hashing to avoid disrupting the chain [25]. The ability to undo human errors is also valuable for enterprise: e.g., if someone accidentally put an API key or password on-chain or a smart contract had a bug that locked funds, an editable ledger could correct that, whereas an immutable one could not. So in sectors like finance, healthcare, or supply chain, where legal compliance, data rectification, and controlled workflows are paramount, redactable blockchains offer a practical advantage [26] [25]. The trade-off is that one must establish strong governance frameworks: Who is allowed to redact? Under what conditions (extraordinary circumstances only, as Accenture noted)? How to prevent abuse of this power? These questions move blockchain from a pure technology realm into the realm of policy and governance. In summary, for compliance and adaptability, redactable blockchains provide a necessary flexibility that vanilla blockchains lack, but it requires carefully balancing trust and verifying that the feature isn’t misused.
In practical deployments, we may also see hybrid approaches. For instance, a blockchain might be mostly immutable but have a prunable side-log for certain data, or use off-chain storage that can be cleaned while on-chain hashes point to it (so the chain data can be changed by changing what it points to). Such approaches are related but slightly different (often called layered redaction or off-chain redaction). Pure on-chain redaction with chameleon hashes is the most direct method and the focus of our discussion here.
Current State of Research on Redactable Blockchains
Redactable blockchain research has rapidly evolved in the past few years as the community grapples with making blockchains more adaptable. After the initial concept introduction around 2016–2017 (Ateniese’s group and Accenture’s prototype [12]), numerous schemes have been proposed, each trying to improve security, decentralization, or performance:
- Rewriting History in Bitcoin & Friends (Ateniese et al.) The seminal 2017 paper “Redactable Blockchain – or – Rewriting History in Bitcoin and Friends” introduced the basic framework of integrating a chameleon hash into a blockchain to enable post-factum edits [27]. It demonstrated how one could take Bitcoin’s blockchain data structure and modify it in a controlled way. This work was foundational and even led to patent filings [19]. However, it assumed a permissioned context or a trusted party (key holder) to perform redactions, which might not sit well in open blockchains.
- Fine-Grained Redaction & Policy-Based Hashes: Subsequent research (e.g., Derler et al., 2018– 2019) introduced policy-based chameleon hashes (PCH) [28] and fine-grained control over what can be redacted. Instead of one master key for all data, these approaches enforce policies – for example, only certain fields or transactions can be edited and only with certain approvals. PCH essentially embeds conditions into the hash function (like requiring a proof or a certain role to use the trapdoor) [28]. Another work by Ateniese’s team addressed key exposure: how to rotate or update chameleon hash keys if they are leaked (so that a stolen trapdoor can be revoked) [22].
- Permissionless Redactable Blockchains: A big leap was adapting redaction to public (permissionless) blockchains where no single authority exists. The paper by Deuber, Magri, and Thyagarajan (IEEE S&P 2019) proposed consensus-governed redactions . Their protocol allowed [18] Bitcoin-like networks to agree on redactions via a voting mechanism and demonstrated a proof-of-concept with minimal performance overhead [29]. This showed that even in decentralized cryptocurrencies, redaction is conceptually possible if the community is willing to bake in such governance.
- “RedactChain” and Moderation Schemes: More recently, researchers have looked at practical implementations. RedactChain (Matzutt et al.) is a 2023 prototype focusing on swift and transparent removal of illicit content on a blockchain [30] [16]. It uses periodically elected juries of blockchain nodes to decide on redactions, combining chameleon hashes with threshold cryptography for joint collision generation [16]. Multiple juries operate in parallel to quickly respond to reports of bad content, and their actions are recorded in a global redaction log for transparency [31]. The evaluation of RedactChain showed that this kind of moderation layer can be added with only modest overhead per block [32]. Essentially, it’s bringing content moderation (a familiar concept in Web2 platforms) to decentralized ledgers – but in a way that doesn’t undermine the chain integrity.
- Scalability and Performance Improvements: There’s ongoing work on making redaction more efficient and secure. For example, a scheme called OREVI_PCH (2023) targets Internet of Things (IoT) applications, where devices might have limited resources. OREVI_PCH stands for Optimized Resource-Efficient Redaction with Integrity Validation in Policy-based Chameleon Hash. Its implementation (available in a Python prototype [33]) shows how to reduce the computational cost of hashing and collision-finding, making redaction feasible even on lightweight nodes, while ensuring that any redaction still proves the data owner’s honest intent [34] [35]. Other works explore post-quantum secure chameleon hashes (to prepare for a future where quantum computers might break traditional hashes) [36], or on-demand key generation so that each redaction uses a fresh trapdoor to limit exposure.
- Anonymous and Public Redactable Chains: Another frontier is maintaining user anonymity and decentralization. An interesting example is AeRChain (2023) – an Anonymous and Efficient Redactable Blockchain scheme in a Proof-of-Work setting [37]. AeRChain aims to let miners redact blocks without revealing which miner did it, preserving anonymity, and does so efficiently so that the redaction process doesn’t bog down the PoW consensus [37]. This indicates the community’s attempt to reconcile privacy and redaction, which initially seem at odds (since editing implies some authority).
- Surveys and Comprehensive Reviews: Given the flurry of proposals, there have been surveys (like one in Future Internet, 2023 [38] and another focusing on IoT [39]) summarizing challenges and mechanisms. These identify open issues such as: how to prevent the trapdoor from becoming a central point of failure, how to handle transactions vs. blocks (fine-grained transaction redaction might be preferable to rewriting whole blocks), how to ensure consistency of state (especially in UTXO-based ledgers) after a redaction, and how to manage multiple redactions over time.
Finally, practical experimentation is underway. For example, an open-source project by a developer known as Ken Lina on GitHub provides a working prototype of a redactable blockchain implementation (likely to test these concepts). Such prototypes allow researchers and enthusiasts to play with the technology hands-on – to see a blockchain where you can actually edit a block and watch the hash links update accordingly. These implementations are invaluable for finding real-world issues, such as performance bottlenecks or security loopholes, that pure theory might miss. (At the time of writing, we reference Ken Lina’s project as an example, though many others exist, such as the RedactChain codebase [41] and Shams et al.’s OREVI_PCH code [33])
In summary, the state of research on redactable blockchains is vibrant and active. We have moved from basic feasibility demos to robust frameworks tackling decentralization, anonymity, efficiency, and now even the offensive uses of redaction. It’s an exciting intersection of cryptography, distributed systems, and policy. Next, we turn our attention to one of the most intriguing implications raised by researchers: using redactable blockchains as a vehicle for covert channels.
Covert Channels via Redactable Blockchains
What is a covert channel?
In cybersecurity, a covert channel is a communication method used to transfer information in a way that violates the system’s security policy or intent, by exploiting some unintended or hidden medium [42]. In plainer terms, it’s like sending secret messages using the system’s normal operations as cover, where no explicit communication channel exists for that purpose. Classic examples include two processes on a computer coordinating via timing CPU usage or modifying seemingly innocuous files to signal bits of data – all without the system’s security mechanisms realizing information is being exchanged. Covert channels can be categorized mainly into storage channels (where one process writes data to some shared storage that another can read, unbeknownst to the system) and timing channels (where information is encoded in the timing of events or resource usage) . They are typically difficult to detect because they piggyback on legitimate behavior of the system, [43] sending data in small, inconspicuous parts that administrators or observers might overlook [42]. The concept dates back to at least 1973 (Lampson’s work) and often comes up in high-security systems where strict access controls are in place - attackers then resort to covert channels to smuggle information.
So how does this relate to blockchains, especially redactable blockchains? Blockchains are, by design, highly deterministic public ledgers. On a normal blockchain, if one wanted to hide a message, one could embed data in a transaction (for example, using the Bitcoin OP_RETURN field or by crafting a bogus address to encode text) [44]. Indeed, methods and services exist that systematically insert arbitrary data into blockchain transactions [44] - for instance, people have inserted everything from text memos to images and even PDFs into Bitcoin’s blockchain by encoding them in transaction scripts. However, these are not truly covert; they are more like overt data insertion (steganography in some cases). The data might be encoded in hex, but it’s visible to anyone who looks, and it’s permanently recorded. The only “hiding” is that casual users might not realize that some script is actually ASCII art or a piece of malware, but forensically it can be found, and indeed researchers actively scan blockchains for such inserted data [45].
A covert channel in a blockchain context would mean using the blockchain in a way that outsiders or the system wouldn’t easily recognize as a communication channel, to secretly transmit information. Regular blockchains have limited opportunities for this beyond the data insertion (which is not covert if you know where to look) or perhaps timing of transactions (one could imagine encoding bits by timing when transactions are sent or how fees are structured, but these would be extremely low bandwidth and obvious if patterns are detected).
Redactable blockchains, however, introduce a new and intriguing possibility for covert communication. By their nature, they allow certain actors to make changes in the blockchain that are not immediately apparent to others (except through specific audit mechanisms if in place). This can be subverted to send hidden messages. Let’s break down how:
Hidden Data via Block Changes (Storage Channel): An authorized editor could encode a secret • message into the blockchain by modifying block content in a specific, meaningful way that only the intended recipients know how to interpret. For example, suppose a block originally contains a piece of benign data (or even a dummy transaction). The editor could replace that data with a carefully crafted payload that encodes a message (say, ASCII text or a cipher) while using the chameleon hash trapdoor to keep the block’s hash the same. To the blockchain network and observers, nothing obvious has happened – the chain still validates and unless they compare the content bit-by-bit to an earlier copy, they wouldn’t know it changed. If the system does not publicly log the redaction, this new data is essentially smuggled onto the blockchain ledger. The recipients, who might be monitoring that specific block or position, can read out the message from the new content. This is a covert storage channel using the blockchain’s history as the medium. It violates the intended policy (which would be that edits are only for removing illicit content or similar, not for adding new secret content).
- Timing or Signaling via Redaction Events (Timing Channel): If the redaction process is something that can happen at arbitrary times, an editor could also use the pattern or timing of redactions to encode information. Imagine a scenario in which the mere act of performing a redaction (or choosing not to) in a given time window could signal a binary bit (redaction = 1, no redaction = 0). Over multiple blocks or time intervals, an authorized party could send a binary message. To an outside observer, these might look like routine compliance edits, but to a conspirator who knows to watch a particular sequence of blocks, the pattern yields a hidden message. Granted, this is a low-bandwidth channel – perhaps one bit per block or per day – but covert channels are often low-bandwidth by nature [46]. The key is that the decision to trigger a redaction can be an out-of-band signal. If there’s leeway in what gets redacted (e.g. maybe some content is borderline and could be left or removed), a malicious editor could choose based on the bit they want to send, rather than solely on necessity.
- Exploiting Chameleon Hash Randomness: As mentioned earlier, many schemes include a random nonce r in each block for the chameleon hash. When a block is redacted, r is recomputed to satisfy the new hash. This r value itself could carry information. Since the editor has freedom to pick a collision, they might have degrees of freedom to choose an r that encodes a secret. For instance, perhaps there are many possible colliding pairs (data’, r’) that produce the same hash; the editor could choose the one where r′, when interpreted a certain way, contains a hidden code. If someone is recording the sequence of r values of blocks over time, the pattern of those values could embed a message (similar to how one might hide data in the least significant bits of an image’s pixels in classic steganography). To everyone else, r looks like just a random number each time; only the covert receiver who knows the scheme (which bits, which blocks, how to decode) would extract the message.
Essentially, the very feature that you can change data without anyone noticing via hash collisions is itself an attack surface. A malicious insider (or a group, if threshold is used and they collude) could leverage their redaction privileges to leak information or coordinate secretly. This is a form of insider threat – the system might have been designed with only honest, policy-driven use of redaction in mind, but a clever use turns it into a secret messaging platform.
To illustrate a hypothetical scenario: Consider a private corporate blockchain used by a consortium of banks, with an administrator key that can redact transactions for compliance. An insider at one bank wants to leak confidential information to a competitor. They could encode that info into some innocuous field of a past block (say a reference number field in a transaction) by using the admin key to alter it, and adjust the hash via the chameleon function. The blockchain network sees an “admin edit” but if the policy is that admins can edit without question, they don’t raise alarm. The competitor, who has been tipped off to check block X at a certain date, reads the secret from that field. Meanwhile, auditors might only see that “block X was edited” but not realize that new meaningful data was added – they might assume it was a normal removal of sensitive content or something. If the system doesn’t log differences, the covert message is essentially stored on the blockchain under the guise of a redaction.
Another example: In a permissionless redactable chain with voting, suppose an attacker can influence which transactions get targeted for redaction (maybe by submitting fake “reports” of illicit content). By orchestrating a pattern of redactions across different blocks that weren’t truly necessary, they could signal data. Each redaction might remove some seemingly random data – but the choice of which blocks to redact or the exact dummy data inserted could be encoding a message.
From a broader perspective, using a blockchain covertly is attractive to adversaries because blockchains are globally replicated and hard to take down – a message hidden in a blockchain can’t be easily wiped out by defenders (ironically, unless they have redaction powers themselves!). Also, blockchains often have many eyes but those eyes are looking for financial transactions, not hidden messages, providing a form of “security by obscurity.” The open nature and integrity of blockchain data make it a compelling medium for covert communication $47$ , as one paper on blockchain covert communication noted. In fact, there have been studies on using even normal (immutable) blockchains for covert comms – for instance, by hiding data in transaction ordering or using multiple wallets to signal bits.
A redactable blockchain amplifies this because it provides a method to alter history in-place, which is unusual in most systems. Normally, covert channels might involve writing new data (which leaves traces), but here one can change old data. This could potentially make detection harder: an analyst might not think to compare archived copies of the chain to current ones, especially if the system isn’t supposed to change. In a worst-case scenario, an attacker could even toggle data back and forth (redact one message in, then later redact it out) achieving a form of ephemeral communication that disappears after it’s read – the blockchain ends up looking as if nothing happened (if no scars are left), yet the information was briefly there and could have been received by the target in that timeframe.
All of this suggests that covert channels are a real and novel threat vector in redactable blockchain environments. It doesn’t mean the sky is falling – after all, the ability to do this usually requires the attacker to have redaction privileges in the first place, which ideally are tightly controlled. But it’s a new consideration for system designers: not only must you prevent unauthorized edits, you might need to prevent sneaky uses of authorized edits. For example, one could impose restrictions like “the new data in a redacted block must be a default blank or zero value” to avoid editors inserting arbitrary information. Or require that all redaction actions and the before/after states be audited by an independent party, so any unexplained changes are caught. There’s ongoing research in detecting covert channels in other contexts (e.g., network traffic analysis for timing channels); similar techniques could be applied to monitor blockchain redactions. Still, a sufficiently clever scheme could escape notice, especially if the observers don’t even know to look.
In the next section, we will outline some concrete attack vectors and proof-of-concept ideas that leverage the above concepts, showing how one might implement a covert channel in a redactable blockchain and how such an attack might unfold in practice.
Attack Vectors and Proof-of-Concept Ideas
Building on the discussion of covert channels, here are a few attack scenarios and PoC (proof-of-concept) ideas demonstrating how redactable blockchains could be exploited. These examples are drawn from current implementations or theoretical proposals and serve to highlight where security needs extra care:
- 1. Hidden Message Injection via Authorized Edits: In an implementation where an admin can freely edit blocks (such as a naive Accenture-style setup without strict logging), an attacker with access to the admin key can perform a data injection attack. For a simple proof of concept, one could take an open-source redactable blockchain prototype (e.g., the one by Ken Lina on GitHub or the RedactChain code) and modify the code to allow an extra “note” field in transactions. The attacker (as editor) chooses a block somewhere deep in the chain and rewrites a transaction’s note field to include, say, a base64-encoded secret. After recomputing the chameleon hash, they publish the redacted block. All nodes update this block (since it’s an authorized edit). The secret is now embedded in the blockchain. If questioned, the attacker could claim “oh, we removed some disallowed content in that transaction and replaced it with a placeholder,” when in reality they placed meaningful data. A proof-of-concept demonstration of this could involve embedding a short text message and showing that block hashes remain consistent, and that without looking at historical archives, no one can tell the message wasn’t there all along.
- 2. Covert Signaling with Redaction Events: Another vector is to use the pattern of redactions themselves as the signal (a timing channel or event channel). For example, suppose the redactable blockchain’s governance is that any user can propose content for removal and the committee will evaluate it. A malicious user could start proposing dummy content for removal at specific block heights that correspond to bits in a message. The committee, colluding with the user, approves some and rejects others in a pattern. Example PoC idea: Treat every group of 10 blocks as a window; if a redaction occurs in that window, that’s a “1”, if none, that’s a “0.” Over 100 blocks, you transmit a 10-bit secret. One can simulate this on a private chain to show it working – the “listener” just needs to observe whether a redaction happened in each interval. The challenge here is ensuring the redactions don’t arouse suspicion: they might remove innocuous data (which could itself be the covert message as in vector 1). To make detection harder, the attacker could combine this with real removal requests to mix signal with noise. Still, an observant auditor might notice that a lot of unnecessary redactions are happening. A refinement: vary the type of edit or a parameter of it to encode more bits – e.g., if there are multiple editors, which editor’s key was used could encode information (if that’s not strictly deterministic).
- 3. Multiple-Collision Forking (Theoretical): One aggressive idea: because chameleon hashes allow multiple distinct content to have the same hash, an attacker could attempt to maintain two versions of a block – one with some secret data and one without – that both hash to the same value. They distribute one version of the chain to most users and the alternative version to a specific target (perhaps through a custom node or feed). As long as both versions share all subsequent hashes, both are “valid” chains in terms of consensus (there’s technically no fork at the hash level). This is tricky because in practice nodes will gossip full blocks, and if two nodes have different block content for the same hash, that’s usually not supposed to happen. But consider a partial information scenario: maybe a light client gets a block header and some merkle proof that doesn’t include the covert data, whereas a full node gets the full data. The attacker could try to exploit differences in what certain clients see. This is more of a theoretical exploit since keeping the network in the dark about discrepancies would be hard. However, it highlights a potential issue: if the design doesn’t enforce a single canonical version of a redacted block (e.g., if two committees redacted the same block in different ways and there was a glitch), you could have a consistency problem. A PoC here would be academic – one could intentionally create two colliding blocks offline and demonstrate that a hash-based verification can’t tell the difference. This underlines the need for additional verification (like digital signatures or Merkle root consistency checks) beyond just trusting the hash link.
- 4. Unauthorized Redaction via Key Compromise (Integrity Attack): While not a covert channel per se, it’s worth mentioning as an attack vector: if an attacker manages to steal or crack the redaction trapdoor key (or bribery/collusion gives them control of the required threshold of keys), they effectively gain the power to rewrite the blockchain at will [21]. They could alter transactions (e.g., change the recipient of a past payment) and recompute hashes so the chain continues – a direct violation of integrity. Even if such edits would be noticed eventually (say, balances not matching or audit logs showing something), the attacker might do targeted, subtle changes to benefit themselves or cover tracks of a crime. A proof-of-concept for this might use a small private chain where an “attacker” with the trapdoor retroactively changes a transaction that paid someone else into paying themselves, demonstrating that the ledger can be illicitly modified. Mitigations involve strong key protection, multi-party control, and constant monitoring of blockchain state for anomalies. This scenario isn’t about covert communication, but it’s a primary security threat to consider whenever introducing a master key into a blockchain system. It shows the worst-case abuse of redactability – essentially the blockchain could lie.
- 5. Steganographic Encoding in Hash Nonces: This relates to the earlier covert channel point: implementing a PoC where each redaction’s new random nonce r′ is chosen to encode a message. For demonstration, one could set up a toy chameleon hash (there are libraries for this, or use an existing implementation from prior research) and then choose a secret message, break it into bits, and perform a series of redactions where each redaction’s | r^T | value’s binary representation ends in those bits. Then show that someone who knows to read the binary trailing bits of the sequence of | r | values can reconstruct the secret. All the while, the blockchain nodes see only valid hashes. This PoC highlights a covert channel that rides on the numeric values used in the protocol. It’s akin to how one might hide data in the nonce field of Bitcoin blocks (miners could encode messages in block nonces or Coinbase transaction texts – which actually has happened for overt messages). Here it’s the redaction nonce.
- 6. Exploiting Redaction for Malware or Beacon Insertion: Another malicious angle: an attacker could use redactions to insert malicious content or beacons that weren’t there originally. For instance, they might insert a piece of code or a link into a past block such that any client reading that block might execute or flag something. This is less about communication and more about using redaction to introduce covert backdoors. Imagine a smart contract platform where a contract’s code is stored on-chain. An editor could alter a smart contract’s code after deployment to include a vulnerability or backdoor, while keeping the hash consistent. Users interacting with that contract might have no idea it was changed (unless the platform has safeguards). A demonstration might involve a simple script stored on a blockchain that is later changed to a different script via redaction – showing that on-chain code isn’t immutable and could hide a trap. The lesson is that redactable blockchains should ideally notify dependent systems of changes; otherwise, someone could inject malicious data after the fact.
Each of these vectors underscores an important point: with great power comes great responsibility. The power to edit blockchain data must be coupled with robust oversight. Otherwise, attackers (especially insiders) have a new toolkit for wrongdoing. On the flip side, these are largely theoretical or lab-demonstrated attacks at this stage, since redactable blockchains are not yet mainstream. By studying them now, the hope is to bake in defenses from the get-go. For example, one might include covert channel detection as part of the redaction approval process – e.g., analyzing if an edit is attempting to encode external data (maybe by checking that new data is truly random-looking or a prescribed format). Or enforce that all redactions replace data only with some constant (removing information, never adding beyond maybe a fixed template), to limit bandwidth for hidden data.
Conclusion and Implications for Cybersecurity
Redactable blockchains represent a fascinating evolution of distributed ledger technology, one that attempts to reconcile the immutability of blockchains with the real-world need for flexibility and legal compliance. Through mechanisms like chameleon hashing, these systems show that it is technically possible to “have your cake and eat it too” – you can maintain the continuity of the chain (so that it appears immutable and remains cryptographically consistent) while still permitting authorized changes to historical data. This is a powerful capability with clear upsides for scenarios such as removing illicit content from public records, adhering to privacy laws, or correcting operational errors that would otherwise live forever on-chain.
However, as our exploration in this article illustrates, this newfound flexibility introduces non-trivial challenges and risks:
- On the security front, the integrity of the blockchain now depends on the proper management of special keys and processes. It shifts trust: users must trust that the redaction powers are not being abused. If that trust is broken, the whole point of using a blockchain (trust minimization) could be undermined. For public cryptocurrencies, this is almost anathema – hence why such ideas are controversial in those communities. For private/consortium chains, it’s more acceptable but still requires governance. Cybersecurity professionals will need to consider threat models where insiders (or external hackers who gain insider access) have the ability to alter audit logs and records. This is a departure from traditional blockchain threat models that mostly consider external attackers and faulty nodes, rather than a “god mode” insider.
- In terms of transparency and auditability, we must ask: How do we detect and record changes in a redactable blockchain? Solutions like immutable scars or public redaction logs are essential. It might become standard practice to have a “blockchain edit log” akin to version control, so that one can reconstruct the original chain if needed or at least see what was changed. This, in turn, raises interesting questions: If a blockchain is edited to remove illegal content, but we keep a log of that edit (which might include a hash of the removed content or encrypted original), are we still inadvertently preserving the forbidden data? Designing audit logs that are informative but not themselves a liability is an open issue.
- The emergence of covert channels in this context is a prime example of unintended consequences. A feature introduced for legitimate purposes can be repurposed by adversaries in creative ways. This highlights a broader lesson in cybersecurity: whenever we add complexity or new capabilities, we should systematically analyze how they might be misused. The covert channel discussion shows that even something as benign-sounding as “editing a block for compliance” can become a vector for hidden communication. Going forward, research might explore detection mechanisms (perhaps analyzing statistical patterns of redactions, or requiring multi-party review of every edit’s content). It also suggests that any implementation in critical environments should probably constrain what can be done in a redaction to minimize the bandwidth for covert data – for instance, only allowing deletion or zeroization of fields, not arbitrary changes.
- For compliance and legal implications: ironically, while redactable blockchains are designed to help with compliance (like GDPR), they also raise new questions. If a regulator asks for proof that a blockchain record was deleted, a redactable blockchain can comply – but regulators might also worry: “Who can secretly alter records?” It becomes a balance of compliance vs. oversight. Governance frameworks (potentially with legal backing) will be needed to decide who holds redaction keys and how decisions are made. We might see standards or legislation emerge around editable ledgers, just as we have for audit logs in traditional systems (e.g., requiring dual control, approvals, and documentation for any log alteration).
- There are open research questions aplenty. How can we cryptographically ensure that a redaction was authorized? Some ideas involve redaction certificates or proofs that a quorum agreed, which could be attached to the blockchain so that clients know the new block is valid by consensus, not just by hash. Another question: can we make redactions time-bound – e.g., only allow them within X days of data being added (for quick corrections), but not years later? Perhaps using time-lock cryptography on the trapdoor such that its power expires. Also, how do redactable chains interact with smart contracts and stateful systems? If one alters a past transaction, how do we propagate that to contract state? This is complex and might require integrated solutions (some proposals talk about meta-transactions to adjust state consistent with the edit).
- From a performance standpoint, ensuring that the overhead of supporting redactions (extra fields, multi-signatures, etc.) does not degrade the blockchain’s efficiency is another area of focus. Preliminary work shows overhead can be low [48], but each scheme differs.
In conclusion, redactable blockchain technology offers a promising path to more adaptable and legally compliant ledgers, but it must be designed and deployed with great care. It adds a layer of human governance on top of the automated trustlessness of blockchains. This synergy of cryptography with policy can either yield robust systems that handle real-world demands or, if mismanaged, could undermine the very trust that blockchains aim to create. For cybersecurity enthusiasts and professionals, redactable blockchains are a reminder that the field is ever-evolving – even “immutable” ledgers can mutate – and with each innovation, we must vigilantly examine both its benefits and its potential for abuse.
Areas like covert channel prevention, key management, and audit transparency will be crucial in the coming years. There is also a need for more real-world testing: so far, redactable blockchains largely live in prototypes and academic papers. Before they might be adopted in, say, a central bank digital currency or a healthcare record system, they require thorough vetting, perhaps standardization of algorithms (for chameleon hashes, etc.), and clear governance models.
For those interested, the journey is just beginning – and contributions are welcome, whether it’s improving the cryptography (e.g., quantum-resistant redaction functions), building better tooling (maybe “git for blockchain” to track changes?), or developing policies that ensure these editable ledgers remain honest. Blockchains started as a radical idea to trust math over humans; redactable blockchains invite a bit of human discretion back in, hopefully in a harmonious way. Getting that balance right will be key to their success or failure in the cybersecurity landscape.
Further References:
- Arxiv (Deuber et al. 2019) Redactable Blockchain in the Permissionless Setting 18 3
- MDPI Future Internet (Ali et al. 2023) Redactable Blockchain: Comprehensive Review 6 8
- Accenture News (2016) Editable Blockchain Prototype 12 13
- GitHub (COMSYS) RedactChain Prototype 50 16
- NordVPN Glossary Covert Channel Definition 42 43
- MDPI Cryptography (2018) Provably Secure Covert Communication on Blockchain 44
- ResearchGate/Entropy (Ren et al. 2023) AeRChain: Anonymous & Efficient Redactable Blockchain 9. (PoW) 37
- GitHub (shams1310) OREVI_PCH Redactable Blockchain code 33